A prepared technology-dependent company always performs a network vulnerability assessment. It helps them identify security flaws in the network right before cybercriminals exploit them. The main goal of conducting a network assessment is to identify devices on your network that are prone to known vulnerabilities without jeopardizing operating systems.
While network vulnerability assessments can be done manually, it is better to equip your IT staff with tools and software that make their task easier. Conducting periodic vulnerability scans using a vulnerability tool is the perfect addition to performing regular antivirus updates and deploying up-to-date security patches for any new critical network flaws. Regular vulnerability risk assessment scanning immensely helps your organization make sure you discover and mitigate any weaknesses on your network before they can be exploited.
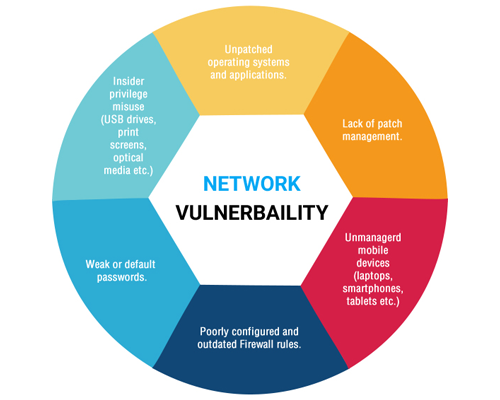
The Definition of Vulnerability Assessment
A vulnerability assessment is a process that helps review and analyze endpoint and device networks for security issues. The assessment may detect network flaws and holes in the network that could leave an opportunity for hackers to exploit. A network vulnerability should also be performed on an ongoing basis as new threats arise and hackers find additional ways to break into systems.
The Importance of Network Vulnerability Assessment Tools
We have mentioned before that adding the right tools is crucial to a successful network vulnerability assessment and can help improve your process. Vulnerability tools are designed to discover which vulnerabilities are present and allow you to resolve these before any hacker takes advantage of them.
Businesses can also choose an open-source vulnerability scanner and managers for their assessments and scanning. You can readily find these network assessment scanners in the market or collect connections through Google. If you have an existing IT maintenance provider or a staff that knows any providers, you can coordinate with them and arrange the requirements you need to get the proper network vulnerability.
Other Supporting Practices in Vulnerability Assessment
Aside from using network vulnerability tools, there are other practices that an effective cybersecurity strategy should have. Here are three crucial practices that an organization should consider:
- Penetration Testing
Although network vulnerability assessment tools can help identify security flaws, they can't determine which security defects cause damage and which do not. That's why penetration tests are crucial to purposefully, but ethically, exploit vulnerabilities and identify which ones are threats.
Unlike malicious hackers, white hat hackers can empower businesses for the better to fix their vulnerabilities before they spiral out of control and lead to major damages. These hackers are proactively searching for loopholes to make computer environments safer and are not breaking into networks and systems for their own personal gain. However, any white hat hacker or penetration tester you hire should have a reputable career in white hat hacking to make sure that he/she is a professional white hat hacker.
-
Ongoing Testing and Security Training
Network vulnerability testing and reporting should be frequent. Your company should establish a routine and strategy that retains your company's safety. Although your IT staff will focus on the actual security assessments, all of them should still partake in security training of their own.
Invest in educating your employees on the latest IT technology, developments, security, and other important factors in maintaining a safe endpoint environment. The more your team understands the threats that can happen every time they boot up their devices, the more likely they are to try and stop an attack before it's too late.
Create Reports Before and After Network Vulnerability Assessment
It is a good practice to always document your vulnerability assessment process from start to finish. Your network vulnerability should also generate an assessment report to interpret and track known vulnerabilities and remediation efforts. This serves as a progress report on what happened to your network and predicts the appropriate changes that you can tweak in the long run.
The report may detail assets and issues in each scan range and report on the findings. From there, your IT team can start refining the details for future project processes and your next assessment.
Conclusion
To sum it up, network vulnerability assessment is made to scan, investigate, analyze, and report on the level of risk associated with any security vulnerabilities discovered on the public, internet-facing devices and to provide your organization with appropriate mitigation strategies to address those discovered vulnerabilities.
Grab the opportunity to enhance your endpoint network using the ITarian Network Assessment Software. Sign up now for free. Just visit our website for more details..