Curious About How Too Spoofing Hacking Works?
Updated on July 15, 2025, by ITarian

Did you know that spoofing is one of the most exploited techniques in cyberattacks? Whether you’re an IT leader protecting infrastructure or a cybersecurity expert responding to threats, understanding how too spoofing hacking works is critical to building defense mechanisms.
Spoofing involves faking or disguising digital identity—such as IP addresses, MAC addresses, or email headers—to deceive users, gain access, or bypass controls. From IP spoofing techniques to full-scale email spoofing attacks, these tactics are central to many phishing schemes, denial-of-service attacks, and intrusions.
This blog post explores how spoofing is used in hacking, common methods, tools, and how IT teams can defend against them.
What Is Spoofing in Cybersecurity?
In cybersecurity, spoofing refers to the act of impersonating a legitimate identity in order to deceive a system or individual. The goal is often to:
- Bypass authentication mechanisms
- Gain unauthorized access
- Redirect traffic
- Launch broader attacks (e.g., malware, phishing, DoS)
Spoofing can be applied across multiple layers of a network or communication system, making it a versatile tactic for hackers.
Types of Spoofing Attacks Explained
Understanding how too spoofing hacking happens starts with the major types of spoofing in real-world cyberattacks:
1. IP Spoofing Techniques
This involves forging the source IP address in a packet header to make it appear as though it came from a trusted source.
Common Use Cases:
- DDoS Attacks: Overwhelm a server by flooding it with requests from spoofed IPs
- Bypassing Firewalls: Impersonate internal addresses
- Man-in-the-Middle (MITM): Intercept data without detection
Defense Tip: Use ingress filtering and packet inspection to detect anomalies.
2. Email Spoofing Attack
This occurs when a hacker forges an email’s “From” address to trick recipients into trusting the source.
Objectives:
- Deliver phishing links or attachments
- Bypass spam filters
- Manipulate users into revealing credentials
Signs of Email Spoofing:
- Unusual domain mismatches
- Typosquatting in sender addresses
- Unexpected password reset links
Defense Tip: Implement DMARC, SPF, and DKIM protocols to validate email authenticity.
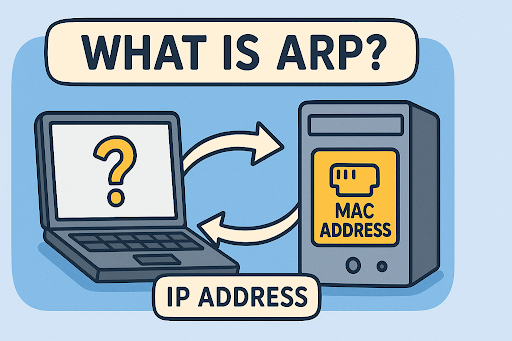
3. MAC Address Spoofing
MAC spoofing changes the device’s Media Access Control (MAC) address to impersonate another device on a network.
Why Hackers Use It:
- Circumvent MAC-based network access control
- Remain anonymous during penetration testing
- Evade tracking in public Wi-Fi networks
Defense Tip: Deploy 802.1X authentication and track MAC address behavior patterns.
4. DNS Spoofing (aka DNS Cache Poisoning)
Attackers manipulate DNS records to redirect traffic from a legitimate website to a malicious one.
Outcomes:
- Phishing page lookalikes
- Credential harvesting
- Malware delivery
Defense Tip: Use DNSSEC to validate integrity of DNS data.
Common Spoofing Tools Hackers Use
Below are some popular tools used for how too spoofing hacking activities (for educational awareness and defense preparedness only):
- Ettercap: Used for ARP spoofing and MITM attacks
- SMBRelay: Targets Windows SMB protocol spoofing
- hping3: Sends custom TCP/IP packets for spoofing IP headers
- Cain & Abel: Spoofs ARP and extracts passwords from cached data
Organizations must monitor for signs of these tools during network traffic analysis.
How Spoofing Impacts Businesses
Spoofing isn’t just a technical nuisance—it has real-world impacts:
- Data Breaches: Leads to unauthorized access to sensitive information
- Financial Loss: Spoofed invoices and emails cause payment redirection
- Brand Damage: Customers lose trust due to impersonation attacks
- Regulatory Risks: Violations of data protection laws (GDPR, HIPAA)
Protecting Against Spoofing Attacks
For IT and Cybersecurity Teams:
- Use Layered Authentication (MFA, biometrics)
- Monitor Network Traffic for irregularities
- Enforce Email Validation Standards (SPF, DKIM, DMARC)
- Apply Firmware-Level Access Controls
- Train Employees on social engineering and spoof detection
For CEOs and Founders:
- Invest in endpoint detection and response (EDR) platforms
- Implement zero trust frameworks
- Conduct regular phishing simulation exercises
FAQ: How Too Spoofing Hacking
Q1: Is spoofing illegal?
Yes. Most spoofing activities—especially for malicious or unauthorized access—are considered cybercrimes under global laws.
Q2: What’s the difference between spoofing and phishing?
Spoofing is the disguise technique; phishing is the scam that uses spoofed communication.
Q3: Can firewalls block spoofing?
Firewalls with packet filtering and intrusion detection capabilities can help detect and block spoofed packets.
Q4: Are MAC spoofers detectable?
Yes, through behavior-based detection systems and correlation with device fingerprinting.
Q5: How do attackers bypass email filters?
They use domain impersonation, font-based obfuscation, and spoofed headers to trick filters.
Final Thoughts: Be Aware, Not Just Secure
Understanding how too spoofing hacking works is not just for ethical hackers or red teamers—it’s critical knowledge for anyone responsible for securing digital infrastructure. Spoofing is an entry point to a wide range of attacks, making awareness and defense strategies more important than ever.
Ready to Fortify Your Systems Against Spoofing?
Enhance your cybersecurity posture with real-time detection, policy enforcement, and endpoint security tools.