What is a Firewall? A Cybersecurity Essential for Modern Enterprises
Updated on June 9, 2025, by ITarian

What is a firewall, and why is it your first line of defense in network security? In today’s digital era, businesses face sophisticated cyber threats daily. According to recent studies, over 60% of small and midsize enterprises experience at least one cyberattack per year. That’s why firewalls are critical—they monitor and control incoming and outgoing traffic based on pre-defined rules, acting as a barrier between your internal network and malicious outsiders.
How Does a Firewall Work?
A firewall works like a gatekeeper between your internal network and the broader internet. It uses a set of rules to filter data packets and decide whether to allow or block them.
Key Functions:
- Packet Filtering: Analyzes data packets based on source/destination IP, port, and protocol.
- Proxy Service: Intercepts requests from clients, masking their identity.
- Stateful Inspection: Tracks the state of active connections to allow only legitimate traffic.
- Content Filtering: Blocks access to unauthorized websites or file types.
This real-time traffic inspection helps organizations reduce the risk of malware infiltration, data breaches, and unauthorized access.
Types of Firewalls Explained
Understanding the various types of firewalls helps in selecting the right one for your organization.
1. Packet-Filtering Firewalls
- Simplest type.
- Examines headers of packets.
- Blocks/permits traffic based on static rules.
2. Stateful Inspection Firewalls
- Keeps track of connection state.
- More secure than packet-filtering.
- Filters based on context and state.
3. Proxy Firewalls (Application-Level)
- Acts as an intermediary.
- Filters at the application layer (e.g., HTTP, FTP).
- Can inspect traffic deeply but may slow down performance.
4. Next-Generation Firewalls (NGFW)
- Combine traditional firewall functions with:
- Intrusion prevention systems (IPS)
- Deep packet inspection (DPI)
- Advanced threat detection
5. Cloud Firewalls (Firewall-as-a-Service)
- Ideal for remote workforces and cloud-native applications.
- Scalable, managed in the cloud.
- Great for hybrid and multi-cloud environments.
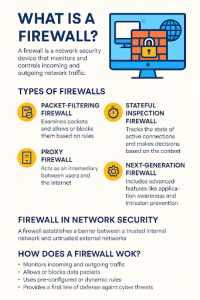
Firewall in Network Security: A Must-Have
Firewalls play a central role in network security by:
- Preventing unauthorized access.
- Blocking malicious websites.
- Reducing the spread of malware.
- Providing visibility into traffic patterns.
- Enforcing organization-wide security policies.
Business Benefits:
- Regulatory Compliance: Helps in meeting standards like HIPAA, PCI-DSS, and GDPR.
- Endpoint Protection: Filters traffic to and from company devices.
- Threat Intelligence Integration: Advanced firewalls sync with threat intel databases for proactive defense.
Firewall vs Antivirus: What’s the Difference?
While both tools are vital to your security stack, they serve distinct purposes.
| Feature | Firewall | Antivirus |
| Purpose | Controls network traffic | Detects and removes malware |
| Level | Network-level protection | Endpoint-level protection |
| Detection | Proactive filtering | Reactive scanning |
| Updates | Rule-based | Signature-based |
| Best Use | Preventing intrusions | Removing infected files |
Pro Tip: For maximum protection, use both. Firewalls prevent malicious traffic, while antivirus software eliminates threats that slip through.
How to Choose the Right Firewall for Your Business
- Assess Your Network: Consider size, complexity, and user needs.
- Identify Assets at Risk: Prioritize protection around sensitive data.
- Set Security Objectives: Do you need intrusion prevention, content filtering, or remote access?
- Decide on Deployment: Hardware-based, software-based, or cloud-based?
- Plan for Scalability: Ensure your firewall grows with your business.
- Integrate With Existing Tools: Make sure it works with your antivirus, SIEM, and VPN tools.
Actionable Firewall Tips for IT Managers and Security Teams
- Regularly update firewall rules and firmware.
- Monitor logs for unusual traffic.
- Use VLANs to segment traffic and reduce internal threats.
- Enable intrusion detection/prevention if available.
- Test firewall configurations with simulated attacks.
Frequently Asked Questions (FAQ)
1. What is a firewall and why is it important?
A firewall is a network security tool that monitors and controls traffic based on rules. It’s essential to block unauthorized access and reduce cyber risk.
2. What are the different types of firewalls?
The main types include packet-filtering, stateful inspection, proxy, next-generation, and cloud firewalls.
3. How does a firewall work with antivirus software?
The firewall blocks suspicious traffic, while antivirus scans files and apps for malware. Together, they offer layered security.
4. Can I use a firewall at home or only in businesses?
Both. Home routers often include basic firewall functions, while businesses use advanced or next-gen firewalls.
5. What’s the difference between software and hardware firewalls?
Software firewalls are installed on devices. Hardware firewalls are standalone units that protect entire networks.
Final Thoughts: Reinforce Your Security With a Firewall
Understanding what a firewall is and implementing the right one can dramatically reduce cyber risk. From filtering malicious traffic to enforcing access controls, firewalls remain a pillar of network defense in modern cybersecurity strategies.
In a world where cyber threats are evolving by the hour, businesses must act proactively.