What is SMB? Understanding the Server Message Block Protocol
Updated on June 18, 2025, by ITarian

Did you know that some of the biggest cybersecurity breaches exploited a protocol that’s been around since the 1980s? If you’re in IT or cybersecurity, understanding what SMB is could be the key to securing your internal networks. Short for Server Message Block, SMB is a critical protocol that enables file and printer sharing between systems in a network. Despite its utility, it’s often a target for cyberattacks due to its vulnerabilities.
In this guide, we’ll unpack what SMB is, how it works, its common uses, SMB port numbers, SMB vulnerabilities, and compare SMB vs NFS—all to help you make better, safer infrastructure decisions.
What is SMB? (Server Message Block Protocol)
Server Message Block (SMB) is a network file sharing protocol that allows applications and users on a computer to read, write, and request services from devices and servers on a network.
Originally developed by IBM in the 1980s, SMB was adopted and extended by Microsoft. Today, it’s most commonly associated with Windows-based systems but has been implemented in various platforms including macOS, Linux, and Unix.
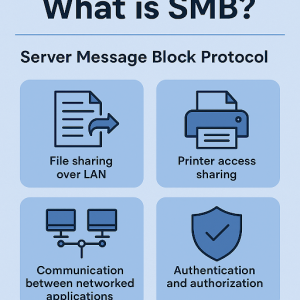
Key Functions of SMB:
- File sharing over LAN
- Printer access sharing
- Communication between networked applications
- Authentication and authorization
How the SMB Protocol Works
SMB works by establishing a client-server communication model. When a user accesses a shared resource on a server (like a file or a printer), the client sends a request using the SMB protocol. The server then processes this request and returns the appropriate data or service.
Key Characteristics:
- Stateful Protocol: Maintains connection between client and server.
- Supports Authentication: Ensures access is granted to authorized users.
- Works Over TCP/IP: Mostly on TCP Port 445.
SMB has evolved significantly through various versions. Here’s a quick look:
| SMB Version | Key Features | Released |
| SMB 1.0 | Original version with basic functionality | 1984 |
| SMB 2.0 | Improved performance and scalability | 2006 (Windows Vista) |
| SMB 3.x | Enhanced security (encryption, performance) | 2012 onwards |
SMB Port Number: Where SMB Lives on Your Network
The SMB port number is critical for network configuration and security:
- TCP Port 445: Used for direct hosting of SMB over TCP/IP (modern standard).
- TCP Ports 137-139: Older versions of SMB over NetBIOS (deprecated).
Knowing these port numbers helps network admins configure firewalls, block unauthorized access, and audit traffic effectively.
SMB Vulnerabilities: A Double-Edged Sword
While SMB is indispensable for many businesses, it’s also a major cybersecurity risk if not configured or patched properly.
Notorious SMB Vulnerabilities:
- EternalBlue (SMBv1):
- Exploited in the WannaCry ransomware attack (2017).
- Took advantage of unpatched SMBv1 vulnerabilities.
- Impacted thousands of systems globally.
- SMBGhost (CVE-2020-0796):
- A critical flaw in SMBv3.
- Allowed remote code execution without authentication.
- Null Sessions:
- SMB allows unauthenticated connections for legacy compatibility, often misused by attackers for enumeration.
Common Attack Vectors:
- Lateral movement inside networks.
- Data exfiltration.
- Ransomware deployment.
Best Practices to Mitigate Risks:
- Disable SMBv1.
- Patch systems regularly.
- Use network segmentation.
- Monitor SMB traffic for anomalies.
SMB vs NFS: Which One is Right for Your Network?
When it comes to choosing a network file-sharing protocol, SMB vs NFS (Network File System) is a common comparison.
| Feature | SMB | NFS |
| Platform | Best on Windows | Best on Unix/Linux |
| Security | Strong with SMB 3.x (supports encryption) | Modern NFS versions support Kerberos |
| Performance | Slightly slower in mixed environments | Better performance in Linux networks |
| Ease of Setup | Easier on Windows systems | Easier on Linux systems |
| Use Cases | Office environments with Windows PCs | Linux servers and applications |
Key takeaway: Use SMB for Windows-heavy environments and NFS for Linux-based systems.
Real-World Use Cases of SMB
1. Corporate File Servers
Companies use SMB to provide centralized file access to employees across departments.
2. Printing Services
SMB helps in sharing printers across an office, reducing hardware costs.
3. Remote File Access
With VPN or secure tunneling, employees can access shared drives remotely via SMB.
SMB and Cybersecurity: What You Need to Do
- Inventory All SMB Services
Conduct a thorough scan of your network to identify SMB services. - Disable Legacy Versions
Turn off SMBv1 entirely. It’s outdated and highly vulnerable. - Implement Network Segmentation
Separate SMB services from other critical systems using VLANs or firewalls. - Use Encryption
Use SMB 3.x features like end-to-end encryption for data in transit. - Audit Logs and Monitor
Set up alerts for suspicious SMB activity such as brute-force login attempts.
FAQ: Frequently Asked Questions About SMB
1. What is SMB and why is it important?
SMB (Server Message Block) is a network protocol used for sharing files and printers. It’s critical for internal communication between systems in a network.
2. Which port does SMB use?
Modern SMB uses TCP port 445. Older versions use ports 137–139 via NetBIOS.
3. Is SMB safe to use?
SMB is safe when configured correctly, using updated versions (SMB 3.x) and proper network controls. Legacy versions like SMBv1 are highly insecure.
4. What’s the difference between SMB and NFS?
SMB is optimized for Windows environments while NFS is preferred in Unix/Linux setups. NFS may offer better performance in Linux ecosystems.
5. Can SMB be used over the internet?
It’s not recommended. Exposing SMB ports to the internet can lead to severe security breaches. Always use VPNs or secure tunneling.
Final Thoughts: Secure Your SMB Environment Now
The Server Message Block protocol (SMB) is an essential component in modern enterprise networks. But with great power comes great responsibility. Poorly configured SMB services are a goldmine for attackers. By understanding what SMB is, how it works, and its risks, you can build a more resilient cybersecurity posture.
Ready to take control of your network’s security?