Introduction: Are Your Devices Really Protected?
Updated on June 16, 2025, by ITarian
Imagine a hacker gaining access to your CEO’s laptop or a malware infection spreading across your entire organization through one compromised endpoint. Scary, right? In today’s connected world, every device—from smartphones to laptops to IoT gadgets—is a potential gateway for cyber threats. This is where endpoint security comes in.
In this guide, we’ll break down what endpoint security is, why it’s essential, and how you can protect your business from costly attacks. Whether you’re an IT manager, CEO, or someone simply interested in cybersecurity, this article has something for you.
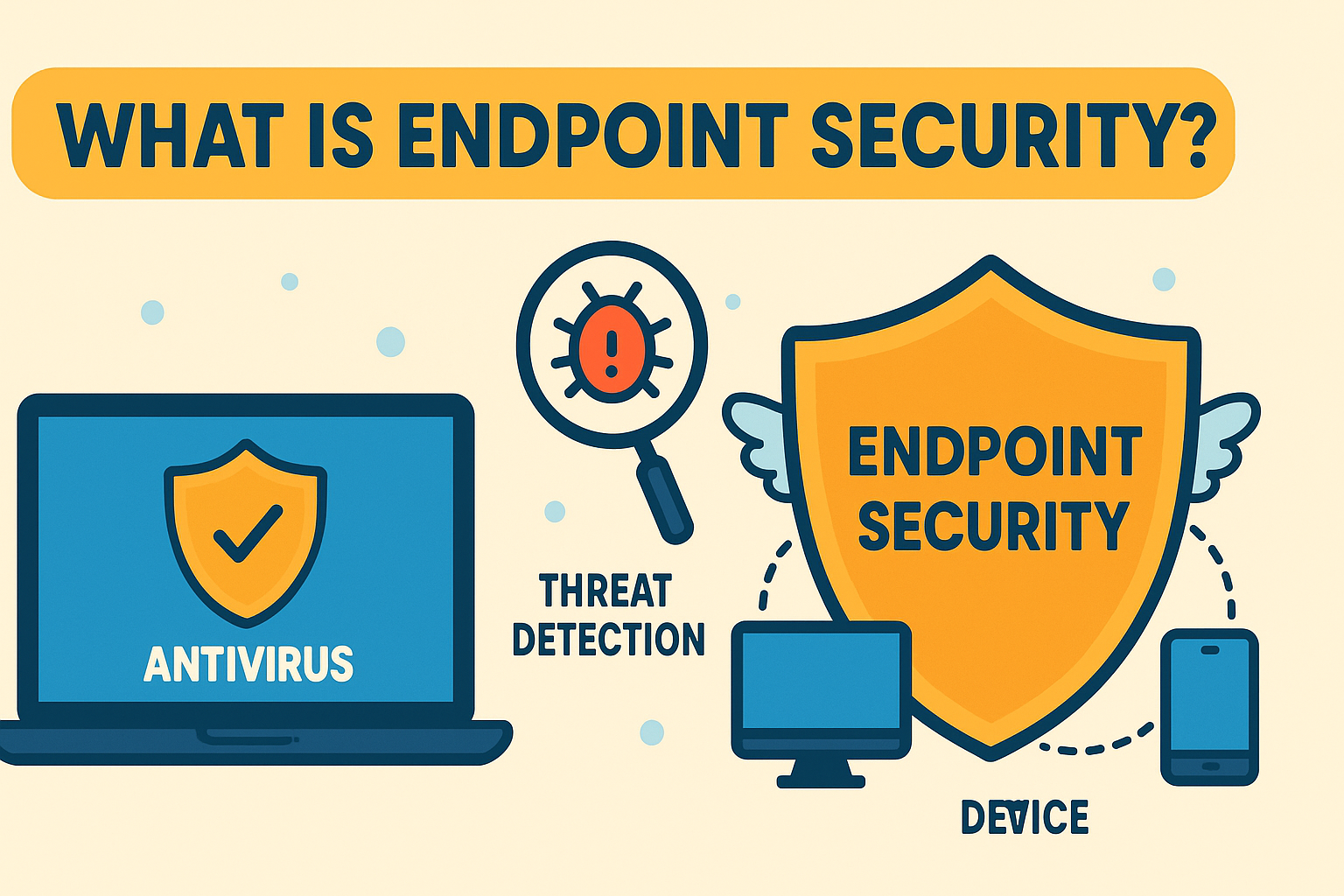
What is Endpoint Security?
Endpoint security refers to the practice of securing end-user devices such as desktops, laptops, mobile phones, and tablets from malicious threats and unauthorized access. It includes a range of solutions, from traditional antivirus software to advanced tools like Endpoint Detection and Response (EDR) and threat detection systems.
The goal? To ensure that every endpoint connecting to your network is protected, monitored, and managed.
Why is Endpoint Security Important?
- Increased Remote Work: With more employees working from home, endpoints are now scattered beyond the corporate firewall.
- Sophisticated Threats: Modern cyberattacks use social engineering, zero-day exploits, and advanced malware.
- Data Protection Regulations: GDPR, HIPAA, and other regulations require businesses to secure user data or face hefty fines.
Key Components of an Endpoint Security Solution
A robust endpoint security solution typically includes:
1. Antivirus and Anti-Malware
The foundation of endpoint security, antivirus software scans files and programs to block malicious activity.
2. Firewall Protection
Helps monitor and control incoming and outgoing network traffic based on predetermined security rules.
3. Threat Detection & Prevention
Modern systems use machine learning and behavioral analysis to detect anomalies and potential threats.
4. Endpoint Detection and Response (EDR)
EDR tools provide advanced visibility, continuous monitoring, and automated response mechanisms to mitigate threats quickly.
5. Encryption
Data encryption ensures that even if a device is compromised, the information remains unreadable to unauthorized users.
6. Device Control
Restricts access to removable media or external devices to prevent data leaks and malware infection.
How Endpoint Security Works
Endpoint security solutions operate through a client-server model or cloud-based architecture. Here’s a simplified breakdown:
- Agent Installation: A software agent is installed on each endpoint.
- Policy Enforcement: Security policies are defined and managed via a centralized platform.
- Monitoring & Alerts: The agent monitors device activity and sends real-time alerts.
- Threat Response: Upon detecting suspicious behavior, the system isolates the endpoint or takes automated action.
This approach ensures holistic protection across all devices and helps security teams respond swiftly.
Endpoint Security vs Network Security
While they sound similar, endpoint and network security address different layers:
| Feature | Endpoint Security | Network Security |
| Focus | Individual devices | Data traffic & infrastructure |
| Examples | Antivirus, EDR | Firewalls, IDS/IPS |
| Control | Device-level | Network-level |
For best results, use both as complementary components of your cybersecurity strategy.
Industries That Benefit Most from Endpoint Security
✅ Healthcare
Protects patient data, ensures HIPAA compliance, and defends against ransomware.
✅ Finance
Safeguards sensitive transactions, account data, and prevents phishing.
✅ Retail
Secures POS systems and customer payment data.
✅ Manufacturing
Protects proprietary designs and connected IoT devices.
✅ Education
Defends against student data breaches and unauthorized access to remote learning platforms.
Choosing the Right Endpoint Security Solution
Here are key factors to consider:
- Scalability: Can it grow with your organization?
- Integration: Does it work well with your existing tools?
- Ease of Use: Is the dashboard user-friendly?
- Support & Updates: Is the provider reliable with patches?
- Advanced Features: Includes EDR, sandboxing, threat intelligence?
Top Benefits of Endpoint Security
- ✔ Reduced Risk of Breaches
- ✔ Enhanced Visibility into Endpoint Activity
- ✔ Improved Compliance
- ✔ Streamlined Incident Response
- ✔ Business Continuity
Common Challenges in Endpoint Security
Despite its benefits, implementing endpoint security isn’t always straightforward:
- BYOD (Bring Your Own Device) Complexity
- Lack of Centralized Control
- Patch Management Delays
- Insider Threats
- Shadow IT Devices
Addressing these requires a mix of policy, training, and robust technology.
Actionable Tips to Strengthen Your Endpoint Security
- Regularly update and patch all endpoints
- Enforce strong password policies
- Train employees on phishing and social engineering
- Use multi-factor authentication (MFA)
- Employ mobile device management (MDM)
Final Thoughts: Stay Ahead of Cyber Threats
In a digital-first world, endpoint security isn’t optional—it’s essential. Cybercriminals are getting smarter, and the attack surface is expanding. Whether you’re a startup founder or an enterprise IT manager, investing in a comprehensive endpoint security solution is your first line of defense.
Ready to protect your business? Sign up for Itarian’s Endpoint Protection Suite today and take the first step toward bulletproof security.
FAQ: Common Questions About Endpoint Security
1. What devices are considered endpoints?
Any device that connects to your network—laptops, smartphones, tablets, IoT devices—is an endpoint.
2. Is antivirus enough for endpoint security?
Antivirus is a good start, but it doesn’t provide real-time threat detection or automated response like EDR.
3. How is endpoint security different from traditional security?
Traditional security focuses on the network; endpoint security protects the actual devices.
4. What is EDR and why is it important?
EDR (Endpoint Detection and Response) offers real-time monitoring, threat hunting, and automated responses to threats.
5. Do small businesses need endpoint security?
Absolutely. Small businesses are increasingly targeted by cybercriminals due to weaker defenses.