Supply Chain Security in Action: Lessons from the CrowdStrike NPM Attack and Why Itarian Provides Stronger Protection
Updated on September 17, 2025, by ITarian

Supply chain attacks are rapidly becoming one of the most dangerous cyber threats facing businesses today. The recent CrowdStrike NPM attack is a powerful reminder of how even leading cybersecurity companies can fall victim to sophisticated tactics.
At Itarian.com, we believe organizations need more than reactive tools. You need a holistic security platform designed to contain threats instantly, protect sensitive data, and secure your entire IT ecosystem. Let’s break down what happened in the CrowdStrike case — and how Itarian delivers stronger supply chain security.
The CrowdStrike NPM Attack: What Happened
In September 2025, multiple npm packages linked to CrowdStrike were compromised in a widespread software supply chain attack. Malicious actors injected code designed to:
- Steal credentials and API tokens from developer environments.
- Exfiltrate sensitive secrets such as environment variables.
- Self-replicate like a worm, infecting downstream dependencies across the npm ecosystem.
Although CrowdStrike quickly removed the packages and clarified that its Falcon product was not directly impacted, the incident revealed the fragility of third-party package ecosystems.
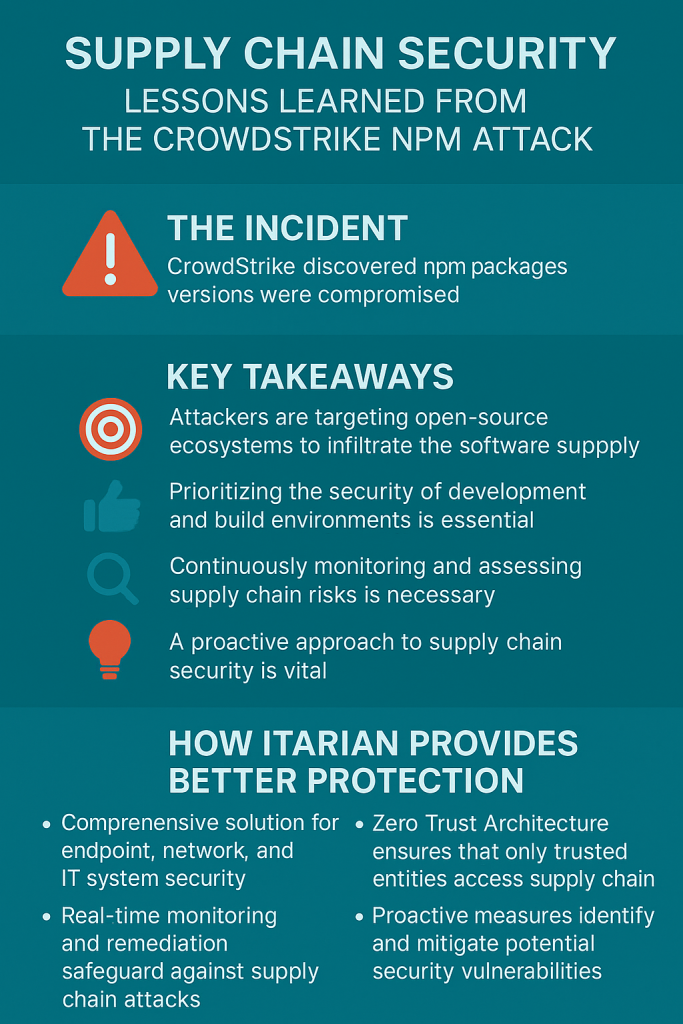
Why Supply Chain Security Matters
Modern businesses rely heavily on open-source software, CI/CD pipelines, and automated updates. These advantages come with hidden risks:
- Trusted-path exploitation: Developers install updates assuming they’re safe.
- Credential compromise: A single stolen token can lead to a full-scale breach.
- Operational disruption: Malicious packages can halt production, compromise customer trust, and trigger compliance failures.
In other words, supply chain attacks don’t just target code — they target the backbone of digital operations.
Itarian vs. CrowdStrike: A Positive Alternative
While CrowdStrike focused on incident response after the npm breach, Itarian builds resilience by preventing, detecting, and containing threats in real time.
| Security Challenge | CrowdStrike Incident | How Itarian Responds |
| Compromised Dependencies | Attackers inserted malicious payloads into npm packages. | Zero-Dwell Containment instantly isolates suspicious processes before they cause damage. |
| Delayed Visibility | Breach discovered after packages were already published. | Remote Monitoring & Management (RMM) detects anomalies in real time, minimizing exposure. |
| Credential Theft | Tokens and secrets were exfiltrated from developer environments. | Endpoint Protection & Policy Enforcement safeguard credentials and prevent unauthorized exfiltration. |
| Ecosystem Risk | Widespread impact on the npm community. | Centralized Governance & Patch Management ensure secure, consistent updates across all endpoints. |
Why Itarian is the Better Choice for Supply Chain Security
- Proactive Endpoint Containment: Malicious processes are isolated automatically — stopping cyber threats before they spread.
- Real-Time Monitoring: Get instant visibility into device health, suspicious activity, and compliance gaps.
- Stronger Credential Protection: Enforce least privilege, rotate tokens, and protect sensitive secrets.
- Unified Platform: From patch management to remote monitoring, Itarian integrates multiple layers of defense in one place.
- Trusted at Scale: Millions of endpoints secured worldwide through Itarian’s proven cybersecurity ecosystem.
Practical Steps to Protect Your Business
In light of the npm supply chain attack, here’s how to strengthen your defenses with Itarian:
- Audit dependencies and secure package sources.
- Enforce least privilege access for developers and admins.
- Automate patch management to avoid vulnerabilities.
- Deploy containment technology to neutralize threats instantly.
- Monitor endpoints proactively with RMM tools.
- Prepare an incident response plan that isolates and remediates affected systems.
Final Thoughts
The CrowdStrike npm attack proves one thing: even the strongest names in cybersecurity can be exposed when supply chain threats strike. But with Itarian’s endpoint containment, supply chain security, and proactive monitoring, your organization gains a crucial advantage — cyber resilience before, during, and after an attack.
👉 Learn more about Itarian’s cybersecurity platform at Itarian.com.
Frequently Asked Questions (FAQs)
1. What is a software supply chain attack?
A software supply chain attack occurs when cybercriminals target the third-party tools, libraries, or services that organizations rely on — such as npm packages, open-source repositories, or CI/CD pipelines. Instead of directly breaching a company, attackers compromise dependencies, allowing malicious code to spread into production environments unnoticed.
2. How did the CrowdStrike npm attack happen?
Attackers gained access to several npm packages associated with CrowdStrike. They injected malicious JavaScript that attempted to steal tokens, credentials, and environment variables from developer systems. The malware also had worm-like properties, enabling it to spread to downstream projects that used the compromised packages.
3. Could endpoint containment have prevented this attack?
Yes. Endpoint containment technology, like the Zero-Dwell Containment feature offered by Itarian, can stop malicious processes the moment they execute. Even if a poisoned npm package is installed, containment ensures that the malware cannot access sensitive data, spread laterally, or cause lasting damage.
4. Why is Itarian better for supply chain security compared to traditional solutions?
Unlike tools that focus mainly on detection after the fact, Itarian delivers proactive security. Features like automated patch management, real-time monitoring, and instant containment reduce both the likelihood and the impact of supply chain breaches. This holistic approach makes Itarian an excellent choice for organizations of any size.
5. What steps should my organization take today to improve supply chain security?
Here are five immediate actions:
- Audit all open-source dependencies and verify their integrity.
- Implement least privilege access for developer accounts.
- Automate updates and patches using a secure platform like Itarian.
- Deploy endpoint protection and containment to neutralize threats in real time.
- Monitor and respond continuously with tools such as Itarian’s RMM.
By combining these practices with Itarian’s security solutions, businesses can build a stronger defense against supply chain threats.