Which of the Following is a Potential Insider Threat Indicator?
Updated on June 3, 2025, by ITarian
When thinking about cyber threats, most people imagine external hackers. But what if the real risk was sitting inside your organization? Which of the following is a potential insider threat indicator is a question that every security-conscious company must be able to answer.
According to Ponemon Institute, insider threats have risen by 44% over the past two years, costing businesses an average of $15.38 million annually. Whether you’re a CEO, IT manager, or cybersecurity analyst, recognizing the red flags of insider threats is essential.
What is an Insider Threat?
An insider threat refers to a security risk that comes from within the organization, typically an employee, contractor, or business partner with authorized access to data and systems.
Insider Threat Definition:
A current or former employee, contractor, or partner who has access to an organization’s data or systems and uses it maliciously or unintentionally to compromise confidentiality, integrity, or availability.
Insider threats are not always malicious. Many result from negligence, lack of awareness, or even coercion by external attackers.
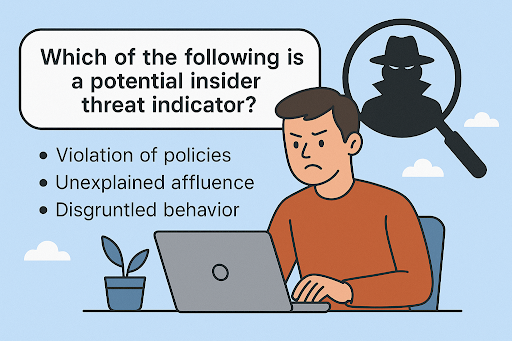
Which of the Following is a Potential Insider Threat Indicator?
Identifying behavioral and digital red flags is crucial. So, which of the following is a potential insider threat indicator? Here are some common and dangerous signals:
Behavioral Indicators:
- Sudden attitude or behavior change
- Unexplained financial gain or lifestyle changes
- Frequent disputes with coworkers or supervisors
- Violation of company policies
- Expressing dissatisfaction with the organization
Technical Indicators:
- Accessing sensitive data not relevant to a job role
- Large data transfers, especially outside business hours
- Using unauthorized devices or software
- Disabling or bypassing security controls
- Unusual login patterns or VPN usage
Spotting just one of these signs doesn’t confirm an insider threat. However, patterns and combinations should trigger deeper investigation.
Types of Insider Threats
Insider threats come in various forms, each requiring different detection strategies.
1. Malicious Insiders
These actors intentionally cause harm, stealing data, sabotaging systems, or leaking confidential information.
2. Negligent Insiders
Employees who mishandle data or fall victim to phishing attacks. They often have no malicious intent but still create significant risk.
3. Compromised Insiders
External hackers gain control of an insider’s account or device and use it to infiltrate systems undetected.
Real-World Examples of Insider Threats
- Edward Snowden (NSA): Leaked classified government documents.
- Anthem Healthcare Breach: Caused by stolen credentials from an internal employee.
- Tesla Employee Leak: Shared sensitive proprietary code with outsiders.
These incidents demonstrate how insider threats can affect both private and public sectors, causing massive financial and reputational damage.
How to Detect Insider Threat Indicators
Proactive detection is key to preventing damage. Here’s how organizations can identify warning signs early:
Monitoring Tools:
- User Behavior Analytics (UBA): Tracks baseline behavior and alerts on anomalies.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the network.
- SIEM Systems: Security Information and Event Management platforms correlate activity across systems.
HR Collaboration:
Work with HR to flag behavioral changes, complaints, or disciplinary actions.
Access Reviews:
Regularly audit who has access to sensitive data and whether that access is justified.
Prevention Strategies for Insider Threats
Prevention isn’t about suspicion—it’s about smart processes and tools. Here are practical strategies:
1. Least Privilege Access
Give employees only the access they need—and no more.
2. Regular Training
Educate staff about secure behavior, phishing risks, and reporting procedures.
3. Multi-Factor Authentication (MFA)
Adds a layer of security to user access.
4. Exit Protocols
Revoke access immediately when an employee leaves the company.
5. Monitor High-Risk Roles
Privileged users and system administrators should undergo extra scrutiny.
Insider Threats by Industry
Every industry is vulnerable, but some are more at risk due to the nature of their data:
- Healthcare: Patient data is highly sensitive and regulated.
- Finance: Insider trading and financial fraud risks.
- Manufacturing: Intellectual property theft.
- Government: National security and classified information.
- Legal: Confidential client documents and case files.
FAQs: Insider Threats
Q1: What is the most common insider threat indicator?
Accessing data not related to one’s job duties is a major red flag and often the first step toward a breach.
Q2: Are insider threats always intentional?
No. Many incidents result from careless behavior or unintentional errors.
Q3: How can small businesses prevent insider threats?
By implementing basic security measures like access controls, employee training, and regular audits.
Q4: Is monitoring employee activity legal?
Yes, within reason and when done transparently. Employers must comply with local privacy laws.
Q5: What role does culture play in preventing insider threats?
A positive workplace culture reduces resentment and increases reporting of suspicious behavior.
Final Thoughts: Trust is Earned, Not Assumed
So, which of the following is a potential insider threat indicator? The answer is: many. But recognizing these signs is only the beginning.
In today’s complex cyber landscape, every organization needs a proactive insider threat detection and prevention strategy. Don’t wait for an incident to happen.
Get started today—Sign up with Itarian and gain access to advanced monitoring, endpoint protection, and behavioral analytics to keep your data safe from the inside out.