Strengthening Cyber Defense With Endpoint Security Services
Updated on January 30, 2026, by ITarian

Every connected device is a potential entry point for cyber threats. From laptops and mobile phones to servers and remote endpoints, today’s distributed IT environments demand stronger protection than ever before. Endpoint security services play a critical role in safeguarding these devices, ensuring organizations can operate securely without slowing down productivity.
As cyberattacks become more targeted and complex, businesses can no longer rely on basic antivirus tools alone. Endpoint security services combine advanced threat detection, real-time monitoring, and centralized management to protect endpoints across the organization. For IT managers, cybersecurity leaders, and executives, understanding how these services work is essential to building a resilient security posture.
What Are Endpoint Security Services
Endpoint security services are managed or software-based solutions designed to protect endpoint devices from cyber threats. These services secure desktops, laptops, mobile devices, and servers by monitoring activity, detecting malicious behavior, and responding to incidents in real time.
Unlike traditional endpoint protection, modern endpoint security services go beyond signature-based detection. They use behavioral analysis, machine learning, and threat intelligence to identify known and unknown threats. This proactive approach helps organizations reduce risk while maintaining operational efficiency.
Why Endpoint Security Services Matter Today
The rise of remote work, cloud adoption, and bring-your-own-device policies has expanded the attack surface for businesses. Endpoint security services help close security gaps by providing visibility and control across all devices, regardless of location.
Without centralized endpoint protection, IT teams struggle to track vulnerabilities and respond to incidents quickly. Endpoint security services simplify this challenge by offering unified dashboards, automated alerts, and coordinated response mechanisms that reduce the burden on internal teams.
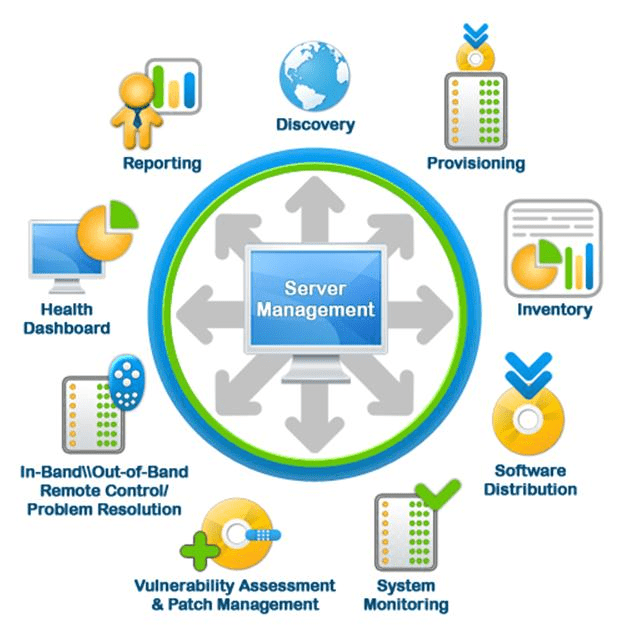
Core Components of Endpoint Security Services
Effective endpoint security services consist of multiple layers working together to protect devices. Each component addresses a specific aspect of endpoint risk, creating a comprehensive defense strategy.
Key components often include endpoint protection platforms, endpoint detection and response, device control, and patch management. Together, these capabilities help prevent breaches, detect suspicious activity, and remediate threats before they spread.
Endpoint Protection vs Endpoint Security Services
Many organizations confuse endpoint protection software with endpoint security services. While endpoint protection focuses primarily on preventing malware infections, endpoint security services offer a broader scope.
Endpoint security services integrate prevention, detection, investigation, and response into a single framework. This allows organizations to respond to advanced threats such as ransomware, zero-day exploits, and fileless attacks more effectively.
How Endpoint Security Services Detect Threats
Modern endpoint security services rely on advanced detection techniques to identify threats early. Behavioral analysis monitors how applications and processes behave, flagging anomalies that indicate malicious intent.
Threat intelligence feeds enhance detection by correlating endpoint activity with known attack patterns. This combination enables faster and more accurate threat identification, reducing the risk of false positives and missed attacks.
Benefits of Managed Endpoint Security Services
Many organizations choose managed endpoint security services to supplement or replace in-house capabilities. Managed services provide access to specialized expertise, continuous monitoring, and rapid incident response.
By outsourcing endpoint security, businesses gain around-the-clock protection without the need to expand internal teams. This approach is especially valuable for small and mid-sized organizations with limited cybersecurity resources.
Endpoint Security Services for Remote Workforces
Remote and hybrid work environments introduce unique security challenges. Devices connect from home networks, public Wi-Fi, and personal locations, increasing exposure to threats.
Endpoint security services ensure consistent protection across remote devices by enforcing security policies regardless of location. This helps organizations maintain compliance and protect sensitive data without restricting workforce flexibility.
Role of Endpoint Security Services in Compliance
Regulatory frameworks often require organizations to protect endpoints and monitor access to sensitive data. Endpoint security services support compliance by providing audit logs, access controls, and automated reporting.
Industries such as healthcare, finance, and government rely on endpoint security services to meet regulatory requirements and demonstrate due diligence during audits. Centralized management simplifies compliance efforts and reduces administrative overhead.
Integrating Endpoint Security Services With IT Operations
Endpoint security services are most effective when integrated with broader IT and security operations. Integration with identity management, SIEM platforms, and network security tools enhances visibility and coordination.
This holistic approach allows security teams to correlate endpoint events with network and user activity. As a result, incidents can be investigated and resolved more quickly, minimizing business disruption.
Endpoint Security Services and Ransomware Protection
Ransomware remains one of the most damaging cyber threats facing organizations today. Endpoint security services play a key role in preventing ransomware attacks by detecting suspicious behavior early.
Advanced services can isolate infected endpoints, stop encryption processes, and roll back malicious changes. This rapid response capability significantly reduces the impact of ransomware incidents.
Choosing the Right Endpoint Security Services
Selecting the right endpoint security services requires careful evaluation of organizational needs. Factors such as device diversity, workforce size, and risk tolerance should guide decision-making.
Organizations should look for solutions that offer scalability, ease of management, and strong threat detection capabilities. A flexible platform ensures that endpoint security services can adapt as business requirements evolve.
Common Challenges in Endpoint Security Management
Despite their benefits, endpoint security services can present challenges if not implemented correctly. Poor visibility, alert fatigue, and complex configurations can hinder effectiveness.
Clear policies, proper training, and ongoing optimization help address these challenges. Regular reviews ensure endpoint security services continue to align with organizational goals.
Future Trends in Endpoint Security Services
Endpoint security services continue to evolve in response to emerging threats and technologies. Artificial intelligence and automation are playing a larger role in threat detection and response.
Future solutions will likely emphasize predictive analytics, zero trust architectures, and tighter integration with cloud-native environments. Staying informed about these trends helps organizations plan for long-term security success.
Best Practices for Maximizing Endpoint Security Services
To get the most value from endpoint security services, organizations should adopt proven best practices. These practices ensure consistent protection and reduce the likelihood of security gaps.
Regular updates, policy enforcement, and user education are critical. Combining technical controls with awareness training strengthens overall endpoint security.
Business Impact of Strong Endpoint Security Services
Effective endpoint security services protect more than just devices. They safeguard business operations, customer trust, and organizational reputation.
By reducing downtime and preventing data breaches, endpoint security services contribute directly to business continuity and growth. Security becomes an enabler rather than an obstacle.
Building a Long-Term Endpoint Security Strategy
Endpoint security services should be part of a broader cybersecurity strategy rather than a standalone solution. Long-term planning ensures consistent protection as the organization scales.
Aligning endpoint security with business objectives helps justify investment and drive adoption. This strategic approach supports sustainable security improvements over time.
FAQs
-
What are endpoint security services
Endpoint security services protect endpoint devices by detecting, preventing, and responding to cyber threats in real time. -
How do endpoint security services differ from antivirus software
They offer advanced threat detection, response, and centralized management beyond basic malware prevention. -
Are endpoint security services suitable for small businesses
Yes, especially managed endpoint security services that provide enterprise-grade protection without large internal teams. -
Do endpoint security services support remote work
They secure devices regardless of location, making them ideal for remote and hybrid workforces. -
How often should endpoint security services be reviewed
They should be reviewed regularly to ensure policies, detection rules, and coverage remain effective.
Final Thoughts
Endpoint security services are a cornerstone of modern cybersecurity strategies. As threats grow more sophisticated and work environments become more distributed, protecting endpoints is no longer optional. By investing in robust endpoint security services, organizations can reduce risk, improve visibility, and maintain operational resilience in an increasingly complex digital landscape.
Take control of your IT environment — begin your ITarian free trial